Scenario 7.
Transparent proxying example: mail virus scanning.
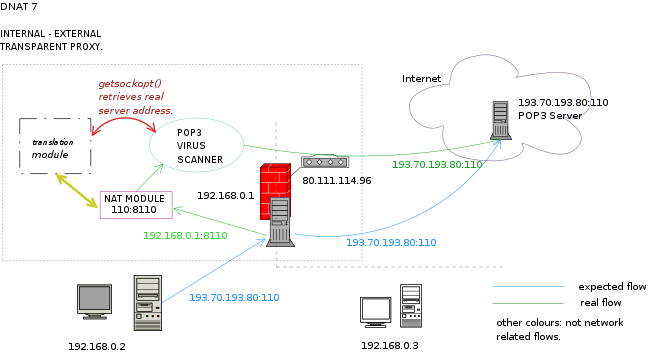
Host 192.168.0.2 wants to receive email from a pop3 server, at address 193.70.193.80.
It does not know about a mail scanner on network gateway, and does not want to bother
about it. This way, all hosts in a private network can download their mail in tranquility, without
having scanning or antivirus software installed.
So, a connection to 193.70.193.80 is started: the packet arrives to the network gateway, to
reach external pop3 server. On the gateway IPFIRE ruleset, there is an indication to change
destination port 110 (pop3) into port 8110, and destination address from real server address
193.70.193.80 to gateway input interface 192.168.0.1. On 192.168.0.1, port 8110 listens the
email scanner: when receiving a connection, it doesn't know real server address automatically,
because the destination address of the packet sent by the email client on host 192.168.0.2
has been changed by nat.
At this point, proxy scanner calls getsockopt function (see
getsockopt() interface for further details) retrieves
from IPFIRE translation tables the original server address and connects to it.
Then mail is retreved and delivered to 192.168.0.2, which safely receives messages.. and
transparently!
In the picture below you can see IPFIRE console output, while in the last picture you can
observe what the email scanner sees from its point of view.

