Port scanning with nmap.
IPFIREwall has been tested with NMAP network port scanner and different online port scanners. So, both ethernet and point to point network interfaces have been tested. A list of scenarios follows and shows results from both scanner side and ipfire side.
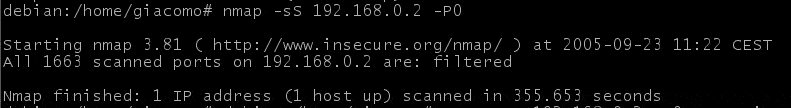
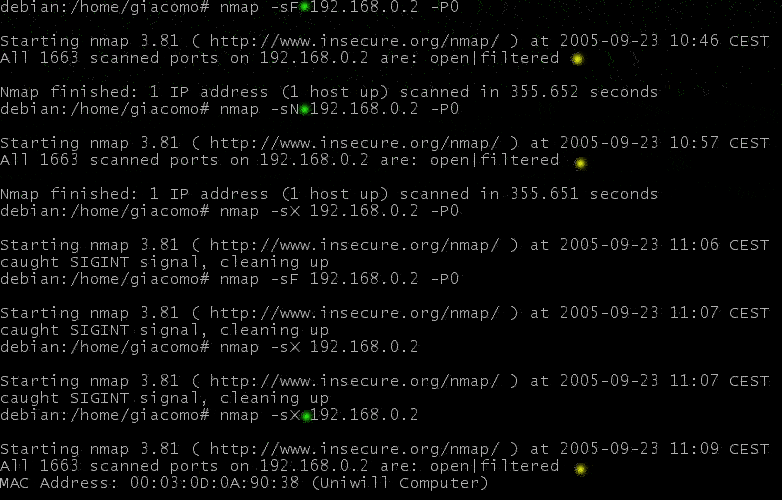
SYN scanning
In SYN scanning, a SYN packet is sent: if a SYN/ACK is received, the port is open. If a RST is received, the port is closed. In this case, since all packets are dropped, no response will be sent back to port scanner by IPFIRE. In this scenario, a particular ruleset has been loaded: 2 rules to allow loopback in both directions and just one stateful rule to let all connections out from IPFIRE host, but no connection in from any node. This is an interesting application of IPFIRE connection tracking. (Really, another rule has been added for UDP, since first was for TCP).
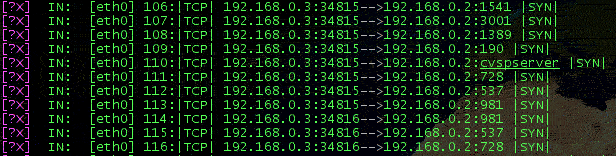
NMAP output after SYN scanning
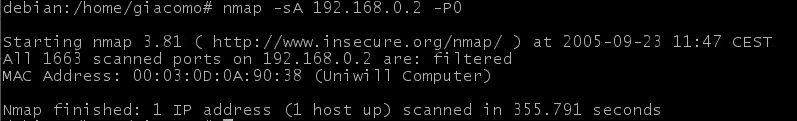
ACK scanning
ACK scanning is an advanced scanning technique that helps determine if a firewall is stateful or simply blocks incoming SYN packets. If nothing comes back, the port is classified as "filtered".
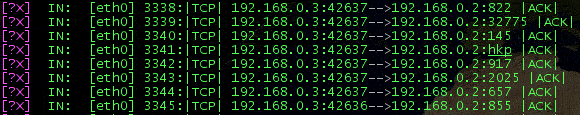
NMAP output is as follows:
FIN scanning
In FIN scanning bare FIN packets are sent. Ports are "open" or "filtered" when nmap fails to elicit any response.
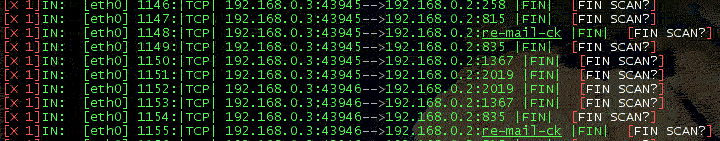
One should wonder how it is that FIN packets are blocked in FIN scanning and
recognized as part of such scan, while normal connections instead work when
in closing state. In fact, in blacklist ruleset a rule has been added
with a row as:
FIN=TRUE
Shouldn't it block also closing connections, when an end host sends a FIN/ACK
packet?
The answer would be yes, if the connection wasn't stateful. Stateful connections are
tracked and checked before blacklist. So good connections are allowed,
bare scans are blocked.
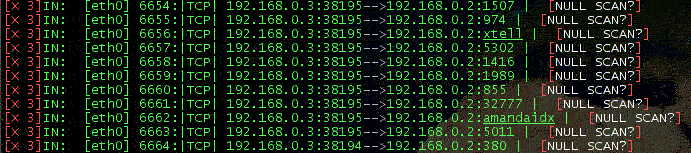
NULL scanning
In NULL scanning, all flags are turned off, as shown in IPFIRE output.
Christmas tree scanning.
In this scenario, FIN, PSH and URG are turned on. Also in this case ipfire correctly detects it.
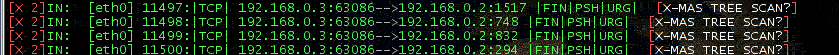
Nmap outputs regarding FIN, XMAS tree and NULL scanning are reported below.
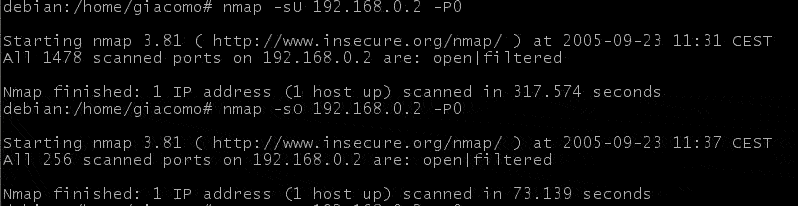
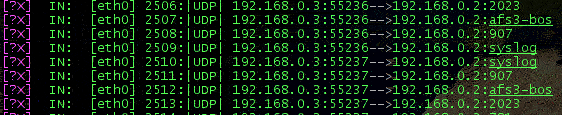
UDP scanning
UDP scanning is aimed to discover UDP open ports. A 0byte UDP packet is sent to each port on the target machine, and if an ICMP host unreachable is received, that port is closed. Of course, no response will go back from IPFIRE, so the result shall be "open|filtered".
IP Protocol scanning
RAW ip packets are sent, without any protocol header. An ICMP protocol unreachable is expected, of course, no response will go back from IPFIRE, so the result shall be "open|filtered".
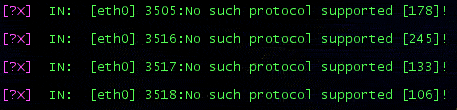
NMAP outputs related to UDP and Protocol scanning are depicted below.